The skill of observing the invisible embedded messages in images, audio, video, text as multimedia and protocols called Steganalysis. An efficient steganalysis method should determine the existence of implanted messages and stego digital image and present some results about the used steganographic algorithm. The challenging problem of this study is a massive quantity of stego hosts to learn valuable knowledge. In this paper, we propose to study several current data mining approaches on steganalysis of images, audio, video, text and protocol. The main aim of this survey is to present the efficiency of using data mining techniques in steganalysis in comparison to the model based steganalysis approaches.
The skill and knowledge of identifying secret message concealed by steganography approach is called Steganalysis. Steganalysis is the skill of detecting the existence of the concealed data in digital images, texts, audios, videos, protocols (Nissar & Mir, 2010). Steganalysis can be categorized into two groups: (a) static and (b) dynamic. Guesstimate some parameter(s) of the embedded algorithm or the secret message is the target of dynamic steganalysis, identifies the existence/non-existence of a secret message is the aim of static steganalysis; in other word these two groups have additional definitions as below:
Static steganalysis: discovering the existence/non-existence of a concealed message in a stego file and recognizing the stego embedded algorithm.
Dynamic steganalysis: guesstimating the implanted message length, position(s) of the concealed message, the secret key used in implanting, some parameters of the stego implanting algorithm and take out the concealed message.
An operation that takes out a number of novel nontrivial patterns included in huge records or databases is called Data Mining. Data Mining includes the utilization of complicated data analysis, which means to find out earlier unidentified, forensic patterns and associations in myriad data set. Therefore, data mining involves analysis, forecast, gathering and organizing data. The aim of data mining is to realize hidden models, unforeseen styles or data, exploiting a mixture of methods from machine learning to bio-inspired meta-heuristic algorithms. Multiple main phases of data mining operation consist of (1) Scope perceptive; (2) Data choice; (3) Data pre-processing, clear out and training; (4) Realizing patterns; (5) Explanation; and (6) Exposure and utilizing revealed facts (Bhatt & Kankanhalli, 2011).
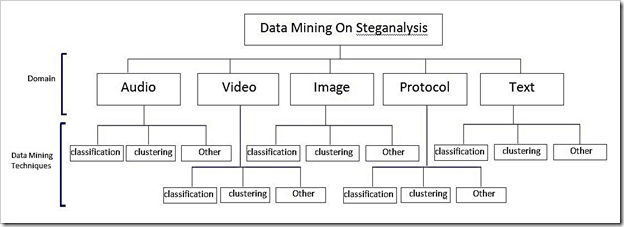
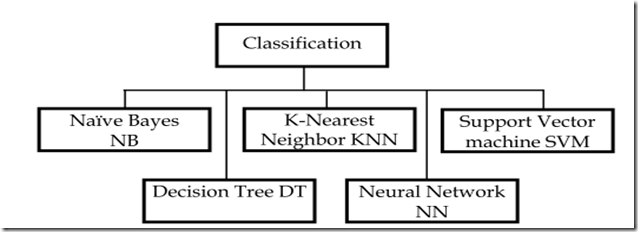
In this study, we will present the survey of using data mining techniques on steganalysis, with intention to establish the significant data mining methods such as classification, clustering and other data mining methods that have been applied for steganalysis purposes. We will review numerous classification methods containing Decision Tree (DT), Support Vector Machines (SVM), Naive Bayes (NB), K-nearest neighbour (KNN), Neural Network (NN) and also a major variety of clustering methods contain K-means, agglomeration and random algorithms.
The rest of this book chapter is organized as follows: In Section 2, we will review the general classification of data mining techniques on steganalysis. Section 3 discusses about applied data mining techniques in brief. In Section 4, we will discuss the applied data mining techniques for image steganalysis. We will study data mining techniques for steganalysis over audio, video, text and protocol domains in section 5. In section 6, we will summarize several previous investigations about the application of data mining techniques for steganalysis using several well-presented figures and tables. Section 7 concludes this book chapter.
Source : ISBN 978-953-51-0840-5